
Sep 17, 2024
Research Topics
In this project, students will develop large-scale AI agents to tackle real-world problems. Our team has previously built AI agents capable of analyzing large-scale system logs to extract insights on system efficiency. We have also developed agents that can automatically test, run, evaluate, and tune real-world applications in real time.
Participants will gain hands-on experience in building AI agents using Large Language Models (LLMs) and contribute to the development of production-grade systems intended for real users.
Preferred Background and Interests

Goal
The objective is to build, deploy, and evaluate production-level AI agents that will be used by real users.
Faculty
Team Mentor: Dong Dai


Sep 11, 2024
FLIE — Flying Labs employing Intelligent Engineering
Research Issues
Autonomous control of a single drone as well as cooperative control of a drone swarm; methods for collecting multispectral images as well as other appropriate remote environment sensors; fusion of sensor collected data and intelligent data processing, volume reconstruction, feature detection, and object tracking; visualization, defect detection, and security applications.
Research Areas
Image processing, multispectral imaging, data fusion, autonomous control, machine learning
Majors Preparation and Interests
Electrical Engineering — signal/image processing, control theory, systems & sensors; Computer Engineering — programming, embedded systems, circuits/systems & sensors; Computer Science — algorithms, programming/software; Mechanical Engineering — control systems; Mathematics — algorithms, stochastic systems
Key Elements
Image Processing, Sensor Fusion, Control Systems, Volume Reconstruction, Object Detection In Images, Adaptive Systems And Machine Learning
Goals
The FLIE — Flying Labs employing Intelligent Engineering — project seeks to develop algorithms, methods, and systems to enable drones that function as autonomous flying labs that address challenging contemporary problems. Challenges addressed include intelligent autonomous control, multifaceted sensing, and data fusion and processing. Intelligent control includes single and cooperative (swarm) drone control. Sensing methodologies include 3D imaging, multispectral imaging, and environmental sensing, with applications spanning visualization, defect detection, and security applications.
Faculty
Ken Barner, Professor, ECE, barner@udel.edu


Sep 11, 2024
Defending next generation mobile and IoT devices
Research Issues
Mobile malware detection techniques; Intrusion detection and protection for embedded systems; Side-channels and covert-channels in mobile and IoT devices, detection and mitigation strategies; Threat analysis and protection strategies for Cyber-Physical Systems.
Research Areas
Mobile computing security; IoT security; Cyber-Physical System security; Trust-oriented embedded system design; Deep learning-based system diagnosis; Security and privacy of emerging devices.
Majors Preparation and Interests
Electrical Engineering – Signal Processing, Machine Learning, Control theory; Computer Engineering – Embedded Systems, Computer Architecture, Mobile Devices, Cybersecurity; Computer Science – Neural Networks, Algorithms, Complexity Analysis, Programming/Software; Mechanical Engineering – Cyber-Physical Systems, Robotics, Dynamics, Control systems; Mathematics – coding, algorithms, complexity analysis.
Key Elements
Programming of mobile, IoT, and embedded devices, Signal processing, Deep learning, Neural networks, Hardware Performance Counters (HPC), Differential power attacks, Energy harvesting devices.
Goals
Internet-of-Things (IoT) is a global information network that allows different smart devices (or “things”) to collect and exchange data seamlessly. What comes with this trend, however, is an Internet-of-Threats: sophisticated attacks can be initiated from any IoT device over the Internet. The fact that these devices are widely deployed in critical applications, such as smart manufacturing, transportation and healthcare, also makes them “ideal” targets for attackers to cause serious damage. This VIP team centers on the study of various cybersecurity threats coming with the global information network, as well as defense of mobile phones, IoT, and embedded devices against these cyberattacks. The team will be working actively on intrusion detection, malware detection and side-channel attacks in mobile phones and embedded devices. The team will collect both digital signals (e.g., hardware performance counters) and analog signals (e.g., dynamic power traces, electromagnetic signals) from the target devices, and adopt signal processing and deep learning techniques for filtering, enhancing, and classifying the obtained signals. The team will also study the security and privacy challenges in energy harvesting devices built with emerging technologies.
Faculty
Chengmo Yang, PhD, Professor, ECE, chengmo@udel.edu
Posters


Mar 20, 2023
Research Issues
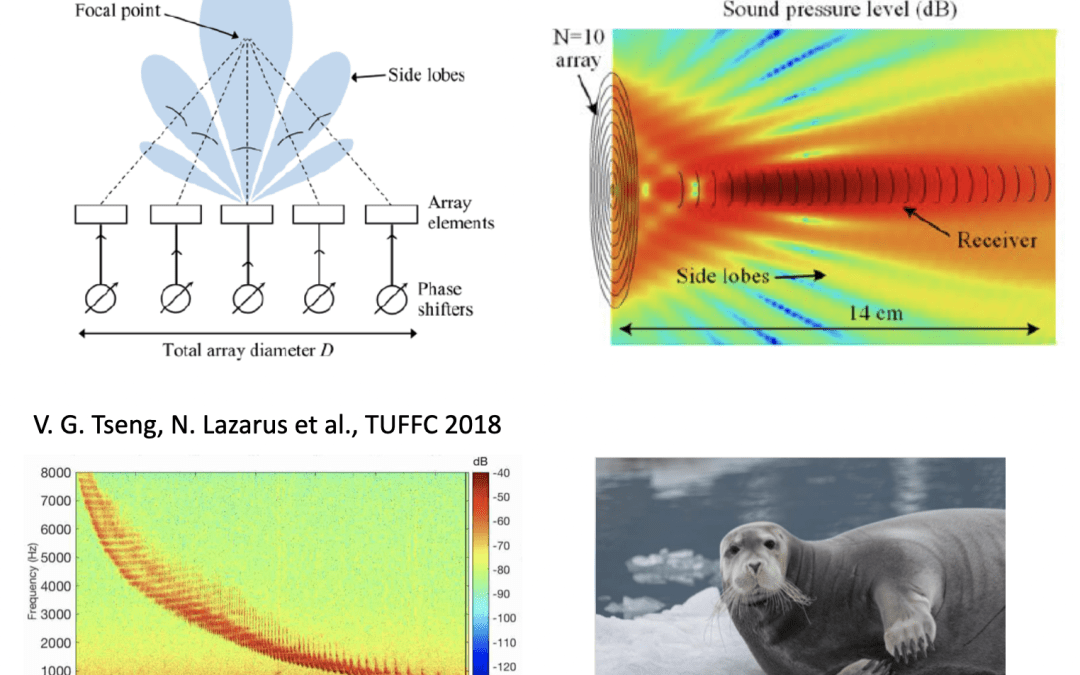
Sound is everywhere in our lives, brought alive by music and conversation. The unique properties of acoustic energy also make it ideal for transmitting energy in many environments from solid metals to the ocean to the human body. This VIP team studies applications of acoustic waves for sensing, communication, energy harvesting and power transfer.
Research Areas
- Musical Acoustic
- Seismic communication
- Acoustic energy harvesting
- Ultrasound for wireless power transfer
- Underwater sound and communications
- Marine and environmental sounds
Majors Preparation and Interests
- EE: signal processing, ML, control, power
- CS: algorithms, programming
- ME: actuation, control, mechanics
- BME: wearables, implantables
Key Elements
Fundamentals of acoustics, transducer design and manufacturing, wireless power transfer, acoustic energy harvesting, sound signal processing and machine learning, musical synthesis.
Goals
The Acoustic Engineering and signal processing laboratory in the Electrical and Computer Engineering Department seeks to develop understanding in a variety of fields related to sound propagation and engineering. These include instrumentation, signal processing and analysis, as well as algorithm development for AI and ML dealing with sound signals.
Faculty
Mohsen Badiey, Professor, ECE, badiey@udel.edu
Nathan Lazarus, Professor, ECE, nlazarus@udel.edu
Mar 20, 2023
Data security for the new age
Research Issues
Lattice‐based Cryptography, Homomorphic Encryption, Post‐quantum Security, Security Proofs, Side‐channel Attacks, Dynamic Message Authentication, Confidential Querying, Network Security, Massively Parallel Computation, Blockchain
Research Areas
Cryptography, Homomorphic Encryption, Penetration Testing, ATM Security, Blockchain Applications, Secure Web Applications
Majors Preparation and Interests
Mathematics – Algebraic Number Theory, Lattice Invariants, Diophantine System Solving, Probabilistic Analysis, Modular Interval Arithmetic CSI – Complexity Analysis, Proofs of Security, Penetration Testing CmpE, CS – Optimizations, High Performance Implementations, Parallel Algorithms, Logic circuit obfuscation, FPGAs, GPUs MIS – Bringing these solutions to market, distributed record management, confidentiality preservation, secure data‐mining
Key Elements
Computational Mathematics, Management Information Systems, Healthcare IT, High‐Performance Computing, Cryptography, Quantum Computing, ATM Security, Biometrics, Pen Testing, Cryptographic Currencies
Goals
The Cloud Crypto team has several aims. We are working actively on ATM security using biometrics, Blockchain voting systems, Penetration Testing, Secure Software Design, and Fully Homomorphic Encryption. Overall, this project aims to create practical and economically disruptive security solutions. Currently, every medical, financial, and governmental institution that must update and search confidential records has to have secure hardware, secure software, and secure staff. They are unable to take full advantage of the internet‐sized economies of scale that drive our modern economy. The central technological hurdle is creating practical security schemes that allow untrusted machines to perform queries and updates on encrypted data. Until very recently this was considered impossible, but in the last few years theoretical, yet infeasible, schemes have been devised. This project aims to push the boundaries of cryptographic applications. From blockchain, to an untrusted cloud, into our post-quantum future. We will need both technological and political breakthroughs to progress.
Faculty
Andy Novocin, PH.D., Professor, ECE, andynovo@udel.edu

Mar 20, 2023
Building tools and technology for critical systems
Research Issues
Developing embedded computer systems to support the safety of electric vehicle charging and robust HWIL testing for imaging systems.
Research Areas
Embedded computers are becoming increasingly pervasive and powerful. They provide functionality for a broad range of systems including household appliances, toys, vehicles, defense systems and medical devices. They surround and sometimes exist inside people. Some of these applications involve critical systems, and the performance of the embedded devices is key to maintaining a safe environment. Performance requirements must be met while maintaining sometimes stringent requirements for power and speed. Electric vehicle charging presents one scenario in which embedded computers are critical for safe operation. Most vehicles today contain dozens of electronic control units (ECUs) which control key systems when the vehicle is driving. To these, electric vehicles add a set of control systems for managing high-power charging, battery management and, in some systems, grid-integration. These systems are also important for maintaining the safety of electric vehicles, and so supporting their increased adoption. Another area in which embedded computers play a key role is that of high speed dynamic displays for hardware-in-the-loop (HWIL) testing of imaging systems. These imaging systems may be integrated in devices used for missile defense. Providing high speed, accurate imagery is key to testing these devices and supporting their development. Testing requires novel displays driven by robust embedded systems.
Majors Preparation and Interests
EE, CE – Electronic circuit design, testing and evaluation of electric circuits and equipment, design, assembly, installation and operation of electric vehicle charging stations.CS – Embedded computing; data analysis and algorithm development
Key Elements
Electric vehicle, Electric grid, Scene projectors, Embedded computing, Computer algorithms
Goals
In this VIP Course we get hands on knowledge of integrated circuits and embedded systems in the electric vehicle industry. We work with many car manufacturers such as ford and BMW to help them create technology for their next generation vehicles.
Faculty
Rodney McGee, Ph.D., Professor, ECE, tmcgee@udel.edu













